
It's not just big organisations who lose millions as a result of cryptocurrency theft, hackers also target individual users to steal small amounts, new data revealed.
According to Chainalysis, the blockchain data platform, scammers stole a record $14bn (£103bn) in cryptocurrency in 2021, with losses from crypto-related crime rising 79% compared with 2020.
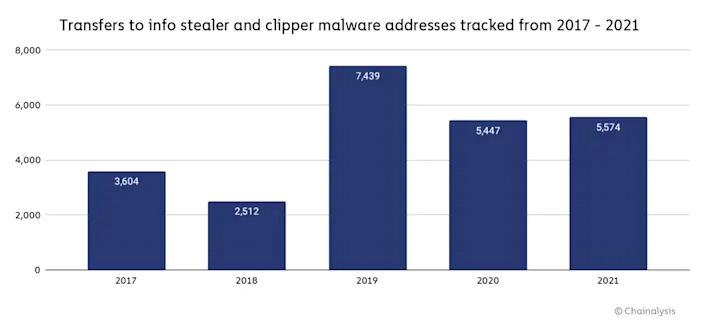
In its latest report it said sophisticated attacks take careful planning and skill to pull off, but through other types of malware, hackers can take a cheaper “spray-and-pray” approach, spamming millions of potential victims and stealing smaller amounts. The malware families sampled received 5,974 transfers from victims in 2021, up from 5,449 in 2020.
It identified found four types of common “cryptocurrency-focused malware families”.
The most dangerous of these is cryptojacking, possibly the most prolific of all malware families, where hackers make unauthorised use of a victim device’s computing power to mine cryptocurrency. In 2020, Cisco’s (CSCO) cloud security division reported that cryptojacking malware affected 69% of its clients.
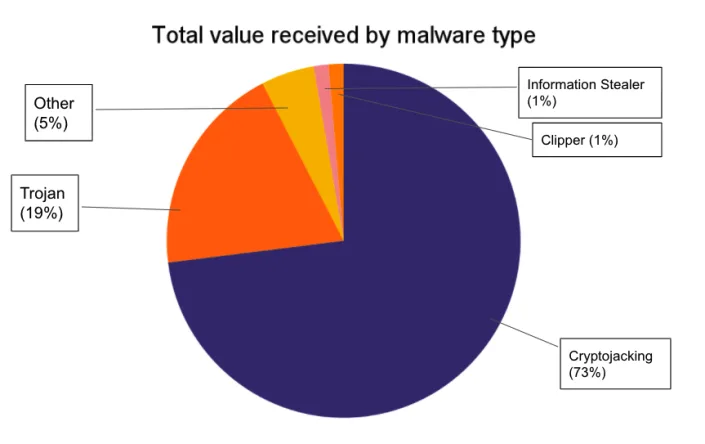
Hackers also love trojans – viruses that look like a legitimate program but infiltrates a victim’s computer.
There are also clippers, which hackers use to replace cryptocurrency addresses copied into a user’s clipboard with their own, allowing them to reroute planned transactions to their own wallets.
A 2018 report from Palo Alto Networks estimated that 5% of all Monero (XMR-USD) in circulation was mined by cryptojackers, which would represent over $100m in revenue. Saleha Riaz
Sun, January 23, 2022, 7:01 PM·4 min read
Inside a data center for cryptocurrency mining with endless racks of CPU and motherboards. Processing the exchange of digital coins.
Inside a data center for cryptocurrency mining. Photo: Getty Images
It's not just big organisations who lose millions as a result of cryptocurrency theft, hackers also target individual users to steal small amounts, new data revealed.
According to Chainalysis, the blockchain data platform, scammers stole a record $14bn (£103bn) in cryptocurrency in 2021, with losses from crypto-related crime rising 79% compared with 2020.
In its latest report it said sophisticated attacks take careful planning and skill to pull off, but through other types of malware, hackers can take a cheaper “spray-and-pray” approach, spamming millions of potential victims and stealing smaller amounts. The malware families sampled received 5,974 transfers from victims in 2021, up from 5,449 in 2020.
It identified found four types of common “cryptocurrency-focused malware families”.
The most dangerous of these is cryptojacking, possibly the most prolific of all malware families, where hackers make unauthorised use of a victim device’s computing power to mine cryptocurrency. In 2020, Cisco’s (CSCO) cloud security division reported that cryptojacking malware affected 69% of its clients.
Chart: Chainalysis
Chart: Chainalysis
Hackers also love trojans – viruses that look like a legitimate program but infiltrates a victim’s computer.
There are also clippers, which hackers use to replace cryptocurrency addresses copied into a user’s clipboard with their own, allowing them to reroute planned transactions to their own wallets.
A 2018 report from Palo Alto Networks estimated that 5% of all Monero (XMR-USD) in circulation was mined by cryptojackers, which would represent over $100m in revenue.
Read more: Live crypto prices
Another type of malware is called info stealer, which collect credentials a user may have saved on their browser. Cryptbot, an infostealer that steals victims’ cryptocurrency wallet details, was the most prolific malware family in this group in 2021, raking in almost half a million dollars in pilfered bitcoin (BTC-USD).
Many of these malware strains are available for purchase on the darknet, making it even easier for less sophisticated hackers to deploy them against victims.
After receiving cryptocurrency from victims, malware operators send the majority of funds on to addresses at centralised exchanges.
However, that majority is slim and getting slimmer. Exchanges only received 54% of funds sent from malware addresses in 2021, down from 75% in 2020. Decentralised finance (DeFi) protocols make up much of the difference at 20% in 2021.
DeFi is a rapidly growing sector that aims to cut out middlemen, such as banks, from traditional financial transactions, like securing a loan. But many of the new protocols being launched have code vulnerabilities that hackers are able to exploit.
Malware attacks aren’t necessarily carried out by the administrators of the malware family itself, but instead are often carried out by smaller groups renting access to the malware family – the report said this is something law enforcement needs to keep in mind.
Studying how cybercriminals launder stolen cryptocurrency may be investigators’ best bet for finding those involved, it said.
Using blockchain analysis, investigators can follow the funds, find the deposit addresses cybercriminals use to cash out, and subpoena the services hosting those addresses to identify the attackers.
Last week Microsoft (MSFT) said it had found destructive malware on dozens of Ukrainian government and private-sector computers which as the ability to wipe computers of data and render them inoperable.
It said there are several reasons why the activity it found was inconsistent with cybercriminal ransomware activity observed by Microsoft.
"Explicit payment amounts and cryptocurrency wallet addresses are rarely specified in modern criminal ransom notes," but were specified in this case, Microsoft said.
Meanwhile, in a separate report Chainalysis said North Korea seems to be the hub of crypto crime.
Hackers in the country launched at least seven attacks on cryptocurrency platforms that extracted nearly $400m worth of digital assets last year.
These attacks targeted primarily investment firms and centralised exchanges, and made use of phishing lures, code exploits, malware, and advanced social engineering to siphon funds out of these organisations’ internet-connected “hot” wallets into North Korea-controlled addresses.
Once North Korea gained custody of the funds, they began a careful laundering process to cover up and cash out.
Yahoo.News